Category: Security

This just in! Couchbase receives SOC 2 compliance certification for Capella.
We know how important security is which is why we're excited to announce that Couchbase Capella has achieved SOC2 compliance.

Announcing Couchbase Autonomous Operator 2.3 Beta
Learn all about the 2.3.0-Beta release of Couchbase Autonomous Operator, including scopes and collections, RBAC changes to Analytics, and self-certification.

Announcing the 3.0 Beta Release for Mobile & Edge Computing
Discover what's new in the 3.0 beta releases of Couchbase Lite and Sync Gateway, such as Kotlin support for Android, SQL++ for mobile, TLS encryption & more.

An Introduction to Edge Computing Architectures
In this overview, Couchbase defines edge computing and demonstrates how to build your own edge architecture. Learn with examples and diagrams here!
![Get Started with Couchbase + Java [Developer Walkthrough]](https://www.couchbase.com/blog/wp-content/uploads/sites/1/2021/10/get-started-couchbase-java-sdk-developer-walkthrough-800x280.jpg)
Get Started with Couchbase + Java [Developer Walkthrough]
In this developer walkthrough, we will look at the basic features of Couchbase – both through a non-relational JSON interface and relational SQL interface.

What Is a (DBaaS): The Importance of Database-as-a-Service
Learn what a Database-as-a-Service is & why it’s a game-changer for cloud-based data management. See how it enables organizations to focus on innovation.

Secure Your Data at Rest with LUKS Disk Encryption in Couchbase
Get an overview of security options in a Couchbase Server cluster and delve into the specifics of data-at-rest security via LUKS on-disk encryption.
Introducing Role-Based Access Control (RBAC) Security for Collections in Couchbase 7.0
Learn how role-based access control, or RBAC Security in the database, has been expanded for Scopes and Collections in the Couchbase Server 7.0 release.
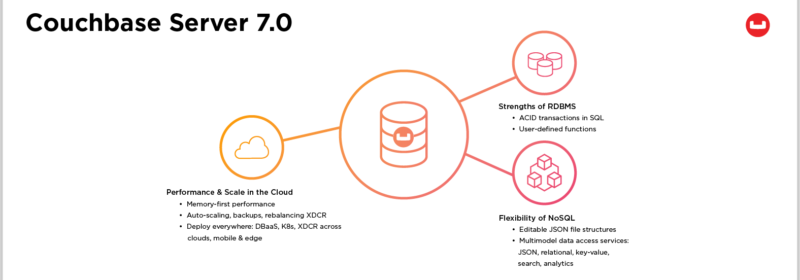
Announcing Couchbase Server 7.0
Discover how Couchbase Server 7.0 delivers the strengths of RDBMS and the flexibility of NoSQL for enterprise applications built for bottom-line results.

Couchbase Autonomous Operator vs MongoDB Enterprise Kubernetes Operator
Discover the key differences between the Kubernetes Operators offered by Couchbase and MongoDB respectively – and which one best fits your enterprise needs.
![OIDC Authorization Code Flow for Client Authentication in Couchbase Sync Gateway [Part 3 of 3]](https://www.couchbase.com/blog/wp-content/uploads/sites/1/2021/07/openid-connect-authorization-code-flow-client-authentication-couchbase-sync-gateway-800x280.jpg)
OIDC Authorization Code Flow for Client Authentication in Couchbase Sync Gateway [Part 3 of 3]
Discover how to build and understand OpenID Connect (OIDC) authorization code flow-based client authentication within Couchbase Sync Gateway replication.
![OAuth 2.0 & OIDC Fundamentals for Authentication & Authorization [Part 1 of 3]](https://www.couchbase.com/blog/wp-content/uploads/sites/1/2021/06/feature-800x280.png)
OAuth 2.0 & OIDC Fundamentals for Authentication & Authorization [Part 1 of 3]
Discover how to implement implicit and authorization code flows for user authentication and authorization using OAuth 2.0 and OIDC alongside Couchbase.
Top Posts
- Data Modeling Explained: Conceptual, Physical, Logical
- Data Analysis Methods: Qualitative vs. Quantitative Techniques
- New Enterprise Analytics Brings Next Generation JSON Analytics to...
- What are Embedding Models? An Overview
- What Is Data Analysis? Types, Methods, and Tools for Research
- What are Vector Embeddings?
- App Development Costs (A Breakdown)
- Column-Store vs. Row-Store: What’s The Difference?
- Application Development Life Cycle (Phases and Management Models)