In the last blog, we described a new feature in Couchbase Server 6.5 called Couchbase groups. In this blog, we will discuss about the new LDAP group capability in Couchbase Server 6.5, along with easy to follow steps to get you started. With the LDAP integration in Couchbase Server, you can leverage your existing organizational structure for managing group-based privileges via RBAC roles.
The particulars of installing, running and configuring the LDAP servers falls outside the scope of this blog; however, to demonstrate a working example, we will use the online LDAP test server (called ldap.forumsys.com) in our configurations.
First, What is LDAP and LDAP groups?
If you’re a system administrator, you probably already know what LDAP stands for, but for those not familiar with LDAP, it means Lightweight Directory Access Protocol, and it manages a hierarchical organization of Users, Groups, and Organisational Units. In the LDAP directory, every object has its own unique path – called a Distinguished Name, or DN. For example, we might have the following DNs for a user and a group respectively –
cn=Perry,ou=Users,dc=example,dc=com
ou=chemists,dc=example,dc=com
LDAP groups are used to group LDAP users together in order to simplify management and maintenance of security outside Couchbase. Typically, a user in Couchbase can take several actions on resources based on the RBAC privileges assigned to the user. For example, an employee might need SELECT access on all buckets. Without LDAP group support, user onboarding involved creating user accounts (domain=external) for every employee, and individually assigning them the SELECT privilege on bucket[‘*’].
With Couchbase 6.5, LDAP groups can be created to bundle users that have similar job roles together in the external LDAP server, and these external LDAP groups can be mapped in Couchbase Server to Couchbase group. Furthermore, privileges via RBAC roles can be associated, and inherited by users who are members of the group.
For example, as shown in the image below, users belonging to Group=workers in the LDAP server, and inside Couchbase Server, the external LDAP workers group is mapped to the employees group. Couchbase roles 1 and 3, are then assigned to the employees group.
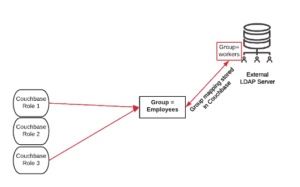
Figure : Fixed roles in Couchbase can be assigned to individual users or groups
LDAP queries and configuration
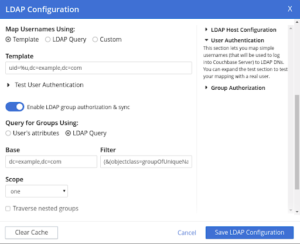
An LDAP query is a command that asks the LDAP directory service for information. For example, if you’d like to see which groups a particular user is a part of, your query is –
Base: dc=example,dc=com
Filter : (&(objectclass=groupOfUniqueNames)(uniquemember=uid=%u,dc=example,dc=com))
Additionally, for the other LDAP fields, you can use the values as shown below –
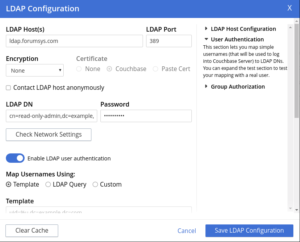
| For more details on connection settings, check here |
Users and groups in Couchbase
In the admin UI of Couchbase, you can now toggle between user and group view in the security tab. You must be either a full administrator, or a security administrator to be able to access the security tab.
Creating a group and mapping it to LDAP group
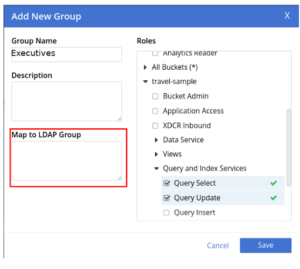
Creating a group and assigning roles to it is easy. By simply clicking ‘Add Group’ in the top right corner of the UI, and picking a group name along with the roles to be associated with the group, you can create a group. If you’re working with an external LDAP server in this case, don’t forget to map this group to the LDAP group.
The map shown in red expects a path to the LDAP group node. For example, if we want to map this to the scientists group in our LDAP server, the map expression would be –
ou=dev,ab=test
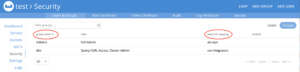
Note that the external mapping for the group refers to an LDAP node path (i.e LDAP group chemists mapped to Couchbase group Employee; LDAP group scientists mapped to Couchbase group Executives, and LDAP group mathematicians mapped to Couchbase group Manager).
Summarizing Group-Role mapping
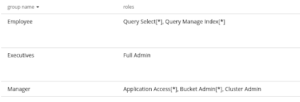
Here is a quick summary of the different groups and role mappings based on our setup so far –
This means that –
1. The Executive is effectively full admin and has all the privileges of Couchbase. This group is mapped to the scientists LDAP group.
2. The Manager has full read-write access on the buckets, as well as cluster and bucket admin privileges. He/she does not have access to security settings. This group is mapped to the mathematicians LDAP group.
- The employee should be able to only issue N1QL SELECT statements for any bucket, and manage indexes. This group is mapped to the chemists LDAP group.
As ‘Tesla’ : the Executive Scientist
Notice that the user logged in is ‘tesla’, which is shown in the top right.
Notice that Tesla is Full admin on the Couchbase cluster
As ‘Euclid’ : the Manager Mathematician
The user logged in is ‘euclid’, which is shown in the top right.
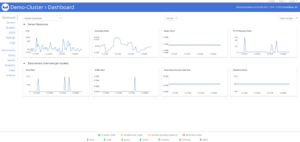
Notice that Euclid cannot change security settings, and the ‘security’ option is not shown in the left menu.
As ‘Curie’ : the Employee Chemist
The user logged in is ‘curie’, which is shown in the top right.
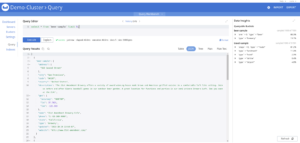
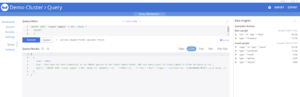
Notice that Curie can issue select statements but not insert statements.
Conclusion
LDAP group support is an exciting new feature in Couchbase Server 6.5. We hope you enjoyed this blog, and as always, we look forward to your feedback. Do take Couchbase Server for a spin and checkout all the new cool features.
Resources
Download
Documentation
Couchbase Server 6.5 Release Notes
Couchbase Server 6.5 What’s New
Blogs
Blog: Announcing Couchbase Server 6.5 – What’s New and Improved
Blog: Couchbase brings Distributed Multi-document ACID Transactions to NoSQL
The Client Settings tab permits the Administrator to include DNS, WINS, and Suffix data while additionally controlling the reserving of passwords, client names, and the conduct of the NetExtender Client. Empower Create Client Connection Profile – The NetExtender customer will make an association profile recording the SSL VPN Server name, the Domain name, and alternatively the username and secret key. You should use a high-quality Vpn like Circuit VPN They are easy to use and cheap also for your security safe.