Na Couchbase, levamos o desempenho muito a sério e, com o lançamento do nosso novo produto, o Couchbase Autonomous Operator 1.0, queríamos ter certeza de que ele é de nível empresarial e está pronto para produção para os clientes.
Nesta postagem do blog, discutiremos os resultados detalhados de desempenho da execução dos testes de benchmark de desempenho do YCSB no Couchbase Server 5.5 usando o Autonomous Operator para implantar na plataforma Kubernetes. Uma das grandes preocupações das empresas que planejam executar o banco de dados no Kubernetes é o "desempenho".
Este documento apresenta uma comparação rápida de duas cargas de trabalho, a saber YCSB A & E com o Couchbase Server 5.5 no Kubernetes versus metal puro.
Carga de trabalho A do YCSB: Essa carga de trabalho tem uma mistura de 50/50 de leituras e gravações. Um exemplo de aplicativo é um armazenamento de sessão que registra ações recentes.
Carga de trabalho E: intervalos curtos: Nessa carga de trabalho, são consultados intervalos curtos de registros, em vez de registros individuais. Exemplo de aplicativo: conversas encadeadas, em que cada varredura é para as postagens em um determinado encadeamento (supostamente agrupadas por ID de encadeamento).
Em geral, não observamos nenhuma degradação significativa do desempenho na execução do Couchbase Cluster no Kubernetes, A carga de trabalho A teve um desempenho equivalente em comparação com o bare metal e a carga de trabalho E teve uma degradação de aproximadamente menos de 10%.
Configuração:
Para a configuração, o Couchbase foi instalado usando a implantação do Operator, conforme indicado abaixo. Para obter mais detalhes sobre a configuração, consulte aqui
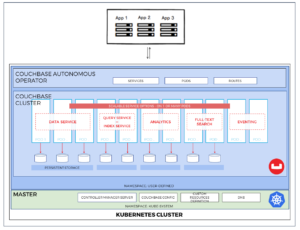
Arquivos:
Implementação do operador: deployment.yaml (consulte o Apêndice)
Implantação do Couchbase: couchbase-cluster-simple-selector.yaml (consulte o Apêndice)
Implantação do gerador de carga de trabalho/cliente: pillowfight-ycsb.yaml (consulte o Apêndice) (imagem oficial do docker do pillowfight do dockerhub e instalação manual do java e do YCSB sobre ela)
Hardware:
7 servidores
24 CPU x 64 GB de RAM por servidor
Configuração do Couchbase
4 servidores: 2 nós de dados, 2 nós de índice+consulta
Cota de 40 GB de RAM para o serviço de dados
Cota de 40 GB de RAM para serviços de índice
1 réplica de dados/bucket
1 réplica de índice primário
Testes:
Carga de trabalhoA e carga de trabalhoE da YCSB
10 milhões de documentos
Fluxo de trabalho após a inicialização de um novo cluster k8s vazio em 7 servidores:
|
1 2 3 4 5 6 7 8 9 |
O # atribui rótulos aos nós para que todos os serviços/pods sejam atribuídos aos servidores corretos: kubectl rótulo nós arke06-sa09 tipo=potência kubectl rótulo nós arke07-sa10 tipo=cliente kubectl rótulo nós ark08-sa11 tipo=cliente kubectl rótulo nós arke01-sa04 tipo=kv kubectl rótulo nós arke00-sa03 tipo=kv kubectl rótulo nós arke02-sa05 tipo=kv kubectl rótulo nós arke03-sa06 tipo=kv |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
#deploy Operador: kubectl criar -f implantação.yaml #deploy Couchbase kubectl criar -f couchbase-agrupamento-simples-seletor.yaml #deploy Cliente(s): kubectl criar -f briga de travesseiros-ycsb.yaml I correu meu testes diretamente de o cliente nó por registro em o doca imagem de o cliente cápsula: doca executar -ele --usuário raiz <briga de travesseiros-yscb contêiner id> bash E instalação YCSB ambiente lá manualmente: apto-obter atualização apto-obter atualização apto-obter instalar -y software-propriedades-comum apto-obter instalar python sudo apto-adicionar-repositório ppa:webupd8team/java sudo apto-obter atualização sudo apto-obter instalar oráculo-java8-instalador exportação JAVA_HOME=/usr/lib/jvm/java-8-oráculo cd /optar wget http://download.nextag.com/apache/mentor/mentor-3/3.5.4/binários/apache-mentor-3.5.4-caixa.tar.gz sudo alcatrão -xvzf apache-mentor-3.5.4-caixa.tar.gz exportação M2_HOME="/opt/apache-maven-3.5.4" exportação PATH=$PATH:/optar/apache-mentor-3.5.4/caixa sudo atualização-alternativas --instalar "/usr/bin/mvn" "mvn" "/opt/apache-maven-3.5.4/bin/mvn" 0 sudo atualização-alternativas --definir mvn /optar/apache-mentor-3.5.4/caixa/mvn git clone http://github.com/couchbaselabs/YCSB |
Executar as cargas de trabalho:
|
1 2 3 4 5 6 7 8 9 10 11 |
Exemplos de YCSB comandos usado em este exercício: Carga de trabalho A Carga: ./caixa/ycsb carregar couchbase2 -P cargas de trabalho/trabalho -p couchbase.senha=senha -p couchbase.host=10.44.0.2 -p couchbase.balde=padrão -p couchbase.upsert=verdadeiro -p couchbase.epoll=verdadeiro -p couchbase.boost=48 -p couchbase.persistTo=0 -p couchbase.replicateTo=0 -p couchbase.sslMode=nenhum -p campos de gravação=verdadeiro -p contagem de registros=10000000 -fios 50 -p tempo máximo de execução=3600 -p contagem de operações=1000000000 Executar: ./caixa/ycsb executar couchbase2 -P cargas de trabalho/carga de trabalho -p couchbase.senha=senha -p couchbase.host=10.44.0.2 -p couchbase.balde=padrão -p couchbase.upsert=verdadeiro -p couchbase.epoll=verdadeiro -p couchbase.boost=48 -p couchbase.persistTo=0 -p couchbase.replicateTo=0 -p couchbase.sslMode=nenhum -p campos de gravação=verdadeiro -p contagem de registros=10000000 -fios 50 -p contagem de operações=1000000000 -p tempo máximo de execução=600 -p arquivo de exportação=ycsb_workloadA_22vCPU.log |
Resultados do teste:
| Env | Configuração direta | Recursos do pod do Kubernetes | Teste | Bare metal | Kubernetes | Delta |
| Env 1 | 22 vCPU, 48 GB de RAM
(os núcleos da CPU e a RAM disponíveis são definidos no nível do núcleo do sistema operacional) |
Limite para:
cpu: 22000m = ~22vCPU mem: 48GB Todos os pods estão em nós dedicados |
Carga de trabalhoA
50/50 get/upsert |
Taxa de transferência: 194,158 req/seg
Média de uso da CPU: 86% de todos os 22 núcleos |
Taxa de transferência: 192,190 req/seg
Média de uso da CPU: 94% da cota da CPU |
– 1% |
| Env 2 | 16 vCPU, 48 GB de RAM
(os núcleos da CPU e a RAM disponíveis são definidos no nível do núcleo do sistema operacional) |
Limite para:
cpu: 16000m = ~16vCPU mem: 48GB Todos os pods estão em nós dedicados |
Carga de trabalhoA
50/50 get/upsert |
Taxa de transferência: 141,909 req/seg
Média de uso da CPU: 89% de todos os 16 núcleos |
Taxa de transferência: 145,430 req/seg
Média de uso da CPU: 100% da cota da CPU |
+ 2.5% |
|
1 2 3 4 5 6 7 8 9 |
Carga de trabalho E: Carga: ./caixa/ycsb carregar couchbase2 -P cargas de trabalho/trabalho -p couchbase.senha=senha -p couchbase.hospedeiro=10.44.0.2 -p couchbase.balde=padrão -p couchbase.upsert=verdadeiro -p couchbase.epoll=verdadeiro -p couchbase.impulso=48 -p couchbase.persistTo=0 -p couchbase.replicarPara=0 -p couchbase.sslMode=nenhum -p campos de gravação=verdadeiro -p contagem de registros=10000000 -fios 50 -p tempo máximo de execução=3600 -p contagem de operações=1000000000 Executar: ./caixa/ycsb executar couchbase2 -P cargas de trabalho/trabalho -p couchbase.senha=senha -p couchbase.hospedeiro=10.44.0.2 -p couchbase.balde=padrão -p couchbase.upsert=verdadeiro -p couchbase.epoll=verdadeiro -p couchbase.impulso=48 -p couchbase.persistTo=0 -p couchbase.replicarPara=0 -p couchbase.sslMode=nenhum -p campos de gravação=verdadeiro -p contagem de registros=10000000 -fios 50 -p contagem de operações=1000000000 -p tempo máximo de execução=600 -p arquivo de exportação=ycsb_workloadE_22vCPU.registro |
| Env | Configuração direta | Recursos do pod do Kubernetes | Teste | Bare metal | Kubernetes | Delta |
| Env 1 | 22 vCPU, 48 GB de RAM
(os núcleos da CPU e a RAM disponíveis são definidos no nível do núcleo do sistema operacional) |
Limite para:
cpu: 22000m = ~22vCPU mem: 48GB Todos os pods estão em nós dedicados |
Carga de trabalhoE
95/5 digitalização/inserção |
Taxa de transferência: 15,823 req/seg
Média de uso da CPU: 85% de todos os 22 núcleos |
Taxa de transferência: 14,281 req/seg
Média de uso da CPU: 87% da cota da CPU |
– 9.7% |
| Env 2 | 16 vCPU, 48 GB de RAM
(os núcleos da CPU e a RAM disponíveis são definidos no nível do núcleo do sistema operacional) |
Limite para:
cpu: 16000m = ~16vCPU mem: 48GB Todos os pods estão em nós dedicados |
Carga de trabalhoE
95/5 digitalização/inserção |
Taxa de transferência: 13,014 req/seg
Média de uso da CPU: 91% de todos os 16 núcleos |
Taxa de transferência: 12,579 req/seg
Média de uso da CPU: 100% da cota da CPU |
– 3.3% |
Conclusões:
O Couchbase Server 5.5 está pronto para produção para ser implantado no Kubernetes com o Autonomous Operator. Desempenho do Couchbase Server 5.5 no Kubernetes comparável à execução em bare metal. Há pouca penalidade de desempenho na execução do Couchbase Server na plataforma Kubernetes. Observando os resultados, a carga de trabalho A teve desempenho equivalente em comparação com o bare metal e a carga de trabalho E teve aproximadamente menos de 10% de degradação.
Referências:
- Cargas de trabalho do YCSB https://github.com/brianfrankcooper/YCSB/wiki/Core-Workloads
- Página do Kubernetes do Couchbase https://www.couchbase.com/products/cloud/kubernetes
- Download do Operador Autônomo do Couchbase https://www.couchbase.com/downloads
- Apresentando o Couchbase Operator https://www.couchbase.com/blog/couchbase-autonomous-operator-1-0-for-kubernetes-and-openshift/
Apêndice
Meu arquivo deployment.yaml
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 |
Versão da API: extensões/v1beta1 gentil: Implantação metadados: nome: couchbase-operador especificação: réplicas: 1 modelo: metadados: rótulos: nome: couchbase-operador especificação: nodeSelector: tipo: potência contêineres: - nome: couchbase-operador imagem: couchbase/couchbase-operador-interno:1.0.0-292 comando: - couchbase-operador # Remova a seção de argumentos se estiver instalando o CRD manualmente argumentos: - -criar-crd - -ativar-atualizações=falso env: - nome: MY_POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadados.espaço de nome - nome: MY_POD_NOME valueFrom: fieldRef: fieldPath: metadados.nome portos: - nome: prontidão-porto containerPort: 8080 readinessProbe: httpGet: caminho: /readyz porto: prontidão-porto initialDelaySeconds: 3 periodSeconds: 3 failureThreshold: 19 |
Meu arquivo couchbase-cluster-simple-selector.yaml
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 |
Versão da API: couchbase.banco de dados.couchbase.com/v1 gentil: CouchbaseCluster metadados: nome: cb-exemplo especificação: imagem de base: couchbase/servidor versão: empresa-5.5.0 authSecret: cb-exemplo-autenticação exposeAdminConsole: verdadeiro antiafinidade: verdadeiro exposedFeatures: - xdcr agrupamento: DataServiceMemoryQuota: 40000 indexServiceMemoryQuota: 40000 searchServiceMemoryQuota: 1000 eventingServiceMemoryQuota: 1024 analyticsServiceMemoryQuota: 1024 indexStorageSetting: memória_otimizado autoFailoverTimeout: 120 autoFailoverMaxCount: 3 autoFailoverOnDataDiskIssues: verdadeiro autoFailoverOnDataDiskIssuesTimePeriod: 120 autoFailoverServerGroup: falso baldes: - nome: padrão tipo: couchbase memoryQuota: 20000 réplicas: 1 ioPrioridade: alta evictionPolicy (política de despejo): fullEviction Resolução de conflitos: seqno enableFlush: verdadeiro enableIndexReplica: falso servidores: - tamanho: 2 nome: dados serviços: - dados cápsula: nodeSelector: tipo: kv recursos: limites: CPU: 22000m memória: 48Gi solicitações: CPU: 22000m memória: 48Gi - tamanho: 2 nome: qi serviços: - índice - consulta cápsula: nodeSelector: tipo: kv recursos: limites: CPU: 22000m memória: 48Gi solicitações: CPU: 22000m memória: 48Gi |
Meu arquivo pillowfight-ycsb.yaml
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
Versão da API: lote/v1 gentil: Trabalho metadados: nome: briga de travesseiros especificação: modelo: metadados: nome: briga de travesseiros especificação: contêineres: - nome: briga de travesseiros imagem: sequoiatools/briga de travesseiros:v5.0.1 comando: ["sh", "-c", "tail -f /dev/null"] restartPolicy: Nunca nodeSelector: tipo: cliente |
Prezado Raju,
É um bom blog.
Por favor, atualize-o um pouco para que seja mais fácil de acompanhar.
Dois comentários:
Comentário#1:
sequoiatools/pillowfight:v5.0.1 parece ter sido desenvolvido no coreos e, portanto, não tem um gerenciador de pacotes, especificamente não tem o apt-get.
Comentário#2
As etapas abaixo não estão funcionando agora, pois houve alguma alteração no contrato de licença do Oracle Java.
sudo apt-add-repository ppa:webupd8team/java
-Obrigado
Instalei o JDK 11.
Recebi o erro abaixo ao usar "-p couchbase.epoll=true"
Carregando carga de trabalho...
Teste inicial.
Tempo máximo de execução especificado como: 120 segundos
ADVERTÊNCIA: Ocorreu uma operação ilegal de acesso reflexivo
AVISO: Acesso reflexivo ilegal por com.couchbase.client.deps.io.netty.util.internal.PlatformDependent0 (file:/opt/ycsb-couchbase2-binding-0.15.0/lib/core-io-1.3.1.jar) ao campo java.nio.Buffer.address
AVISO: Considere a possibilidade de relatar isso aos mantenedores do com.couchbase.client.deps.io.netty.util.internal.PlatformDependent0
AVISO: Use -illegal-access=warn para ativar avisos de outras operações de acesso reflexivo ilegal
AVISO: Todas as operações de acesso ilegal serão negadas em uma versão futura
Aug 23, 2019 9:15:34 AM com.couchbase.client.deps.io.netty.util.internal.PlatformDependent
INFORMAÇÕES: Sua plataforma não fornece uma API de baixo nível completa para acessar buffers diretos de forma confiável. A menos que explicitamente solicitado, o buffer de heap sempre será preferido para evitar a possível instabilidade do sistema.
com.yahoo.ycsb.DBException: Não foi possível conectar-se ao Couchbase Bucket.
at com.yahoo.ycsb.db.couchbase2.Couchbase2Client.init(Couchbase2Client.java:208)
at com.yahoo.ycsb.DBWrapper.init(DBWrapper.java:86)
em com.yahoo.ycsb.ClientThread.run(Client.java:424)
em java.base/java.lang.Thread.run(Thread.java:834)
Causas: java.lang.IllegalStateException: falha ao criar um loop de evento filho
at com.couchbase.client.deps.io.netty.util.concurrent.MultithreadEventExecutorGroup.(MultithreadEventExecutorGroup.java:68)
at com.couchbase.client.deps.io.netty.channel.MultithreadEventLoopGroup.(MultithreadEventLoopGroup.java:49)
at com.couchbase.client.deps.io.netty.channel.epoll.EpollEventLoopGroup.(EpollEventLoopGroup.java:91)
at com.couchbase.client.deps.io.netty.channel.epoll.EpollEventLoopGroup.(EpollEventLoopGroup.java:67)
at com.yahoo.ycsb.db.couchbase2.Couchbase2Client.init(Couchbase2Client.java:195)
... 3 mais
Causado por: java.lang.NullPointerException
at com.couchbase.client.deps.io.netty.util.internal.PlatformDependent0.allocateMemory(PlatformDependent0.java:330)
at com.couchbase.client.deps.io.netty.util.internal.PlatformDependent.allocateMemory(PlatformDependent.java:210)
at com.couchbase.client.deps.io.netty.channel.epoll.IovArray.(IovArray.java:64)
at com.couchbase.client.deps.io.netty.channel.epoll.EpollEventLoop.(EpollEventLoop.java:60)
at com.couchbase.client.deps.io.netty.channel.epoll.EpollEventLoopGroup.newChild(EpollEventLoopGroup.java:106)
at com.couchbase.client.deps.io.netty.util.concurrent.MultithreadEventExecutorGroup.(MultithreadEventExecutorGroup.java:64)
... 7 mais