- Products
-
-
Platform
Self-Managed
-
Services
Capabilities
-
-
-
Why Couchbase?
-
-
- Solutions
-
-
By Use Case
-
By industry
-
By Application need
-
-
- Resources
-
-
Popular Docs
-
By Developer Role
-
Quickstart
-
-
- Company
-
-
About
-
Partnerships
-
Our Services
-
Partners: Register a Deal
Ready to register a deal with Couchbase?
Let us know your partner details and more about the prospect you are registering.
Start hereMarriott
Marriott chose Couchbase over MongoDB and Cassandra for their reliable personalized customer experience.
Learn more
-
-
- Pricing
- Try Free
- Sign In
- English
- search
Enterprise-Grade Security
Get proven enterprise security to protect, detect threats, and respond to your needs.

Learn about Capella’s compliance and certifications
Enterprise-grade data security in Couchbase
Couchbase Server has a full suite of data security features for authentication, authorization, encryption, and auditing to meet the needs of your most critical and sensitive database workloads.
Deliver value to your customers while ensuring their information is safe
Management
Use centrally managed controls to keep data access aligned with your shifting business priorities.
Scale
Ensure your database meets your security needs as it scales.
Integration
Integrate Couchbase’s logging data and monitoring capabilities into your daily tools.
Compliance
Couchbase Capella DBaaS meets your needs for SOC 2, HIPAA, GDPR, PCI DSS, and CSA STAR.
Security key capabilities
The majority of sensitive information is subject to stringent regulations. Couchbase offers a comprehensive array of data security capabilities designed to cater to the demands of your most vital and sensitive database operations.
Authentication (AuthN)
Teams can use built-in technologies, LDAP, Active Directory, x.509 certificates, and other configurable policies.
Authorization (AuthZ)
Users and groups can be assigned roles with role-based access control permissions.
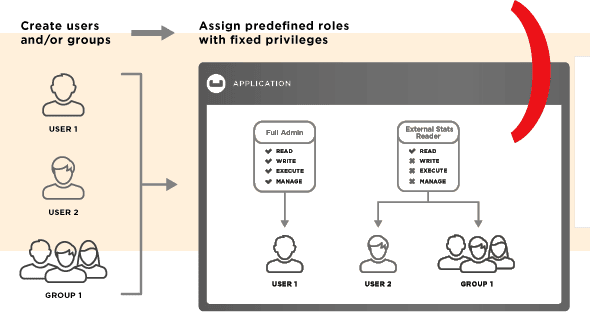
Easy-to-manage user and application access
Couchbase Server’s secure authentication protocols and role-based access control (RBAC) let you align groups of users in a centrally managed system to control access and permissions. Administrators can use granular controls to follow the principle of least privilege, allowing only the minimal required access without additional risk exposure.
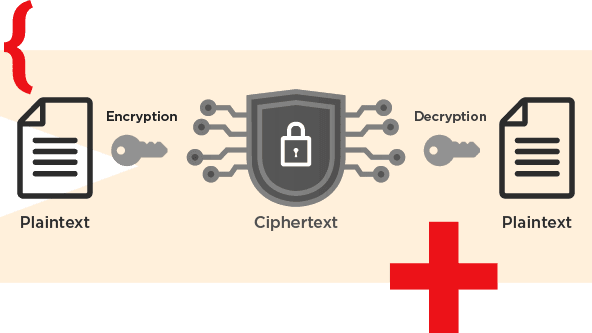
Strong encryption with minimal performance impact
Multiple levels of high-strength encryption protect data at rest, in transit, and in process to meet a wide range of regulatory requirements. Our key security features are available across the entire Couchbase Server set of services to support key-value, OLTP, and OLAP use cases both on premises and when using Couchbase Capella, our SOC 2 compliant DBaaS.
Auditing for rapid situational awareness
Collect and integrate security-related information from Couchbase Server into a corporate SIEM system using a secure REST API and standard JSON data formats. Monitor key system configuration changes and respond to incidents or perform forensic analysis.

What customers are saying
“We found that the replication technology across data centers for Couchbase was superior, especially for the large workloads.”

“Couchbase provides blazing speed thanks to its in-memory processing. And auto-failover raises a replica without losing data if a node fails.”

“Couchbase provides a solution no others do. It gives us the modularity we need with immediate operational simplicity, high performance, and scalability.”
Cloud Trust Center
Access Capella DBaaS whitepapers and review its compliance achievements.
Explore related resources

Couchbase Capella security and data protection

Best practices for data protection and security with Couchbase

Security REST API
Start building
Check out our developer portal to explore NoSQL, browse resources, and get started with tutorials.
Use Capella free
Get hands-on with Couchbase in just a few clicks. Capella DBaaS is the easiest and fastest way to get started.
Get in touch
Want to learn more about Couchbase offerings? Let us help.