In part 1 of this 3 part series we learned about the components of TLS, in part 2 we will see how the TLS components interact with each other. In Part 3 of this guide, we’ll see how the components are used in Couchbase Server.
Certificate Signing Process
Whether you are managing your own in-house Certificate Authority, or using an established commercial vendor such as DigiCert, GlobalSign or GoDaddy the first stage is to generate a Certificate Signing Request. Any time a new certificate or a replacement certificate needs to be issued, the entity requesting the certificate generates a key pair consisting of a private key and a public key themselves, typically using the OpenSSL package. In a Couchbase Server Cluster the entity would be an individual Couchbase Server Node. The private key is kept securely by the entity, while the public key is included in a certificate signing request (CSR) which is sent to the CA. Typically this is performed with an intermediate CA not a root CA.
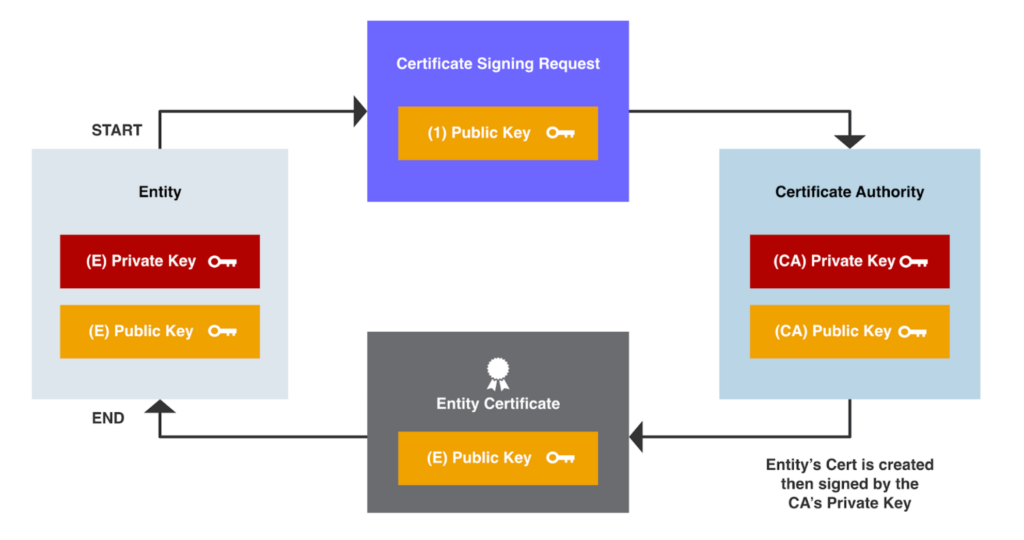
Upon receiving the CSR, the CA verifies the identity of the entity by employing various validation methods, such as domain validation or organization validation. Once the identity is confirmed, the CA generates a digital signature using its private key, which binds the entity’s public key with its identity information. This signed certificate is then returned to the entity.
Certificate Validation
To validate a certificate, the relying party (e.g., a web browser) needs to ensure that the certificate is genuine and issued by a trusted CA. This process involves a series of steps, including the following four stages.
Trust Anchor
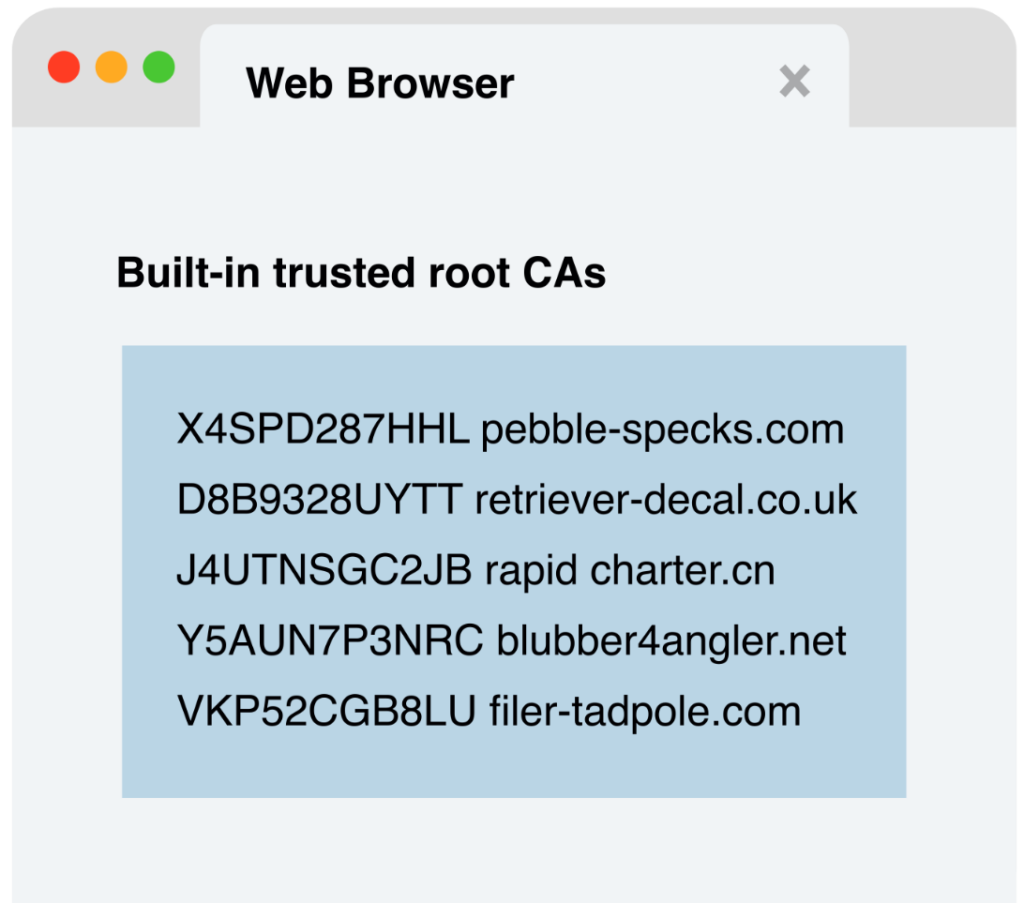
The relying party, for example a web browser, possesses a pre-installed set of trusted root certificates, also known as trust anchors. These certificates belong to well-known CAs and contain their public keys, this serves as the foundation of trust.
When a client or server receives a certificate during the SSL/TLS handshake, it checks if the certificate’s digital signature can be validated by any of the trust anchors installed in the system. If the certificate chain can be traced back to a trust anchor, the certificate is deemed genuine, and the TLS connection proceeds with confidence.
Certification Path
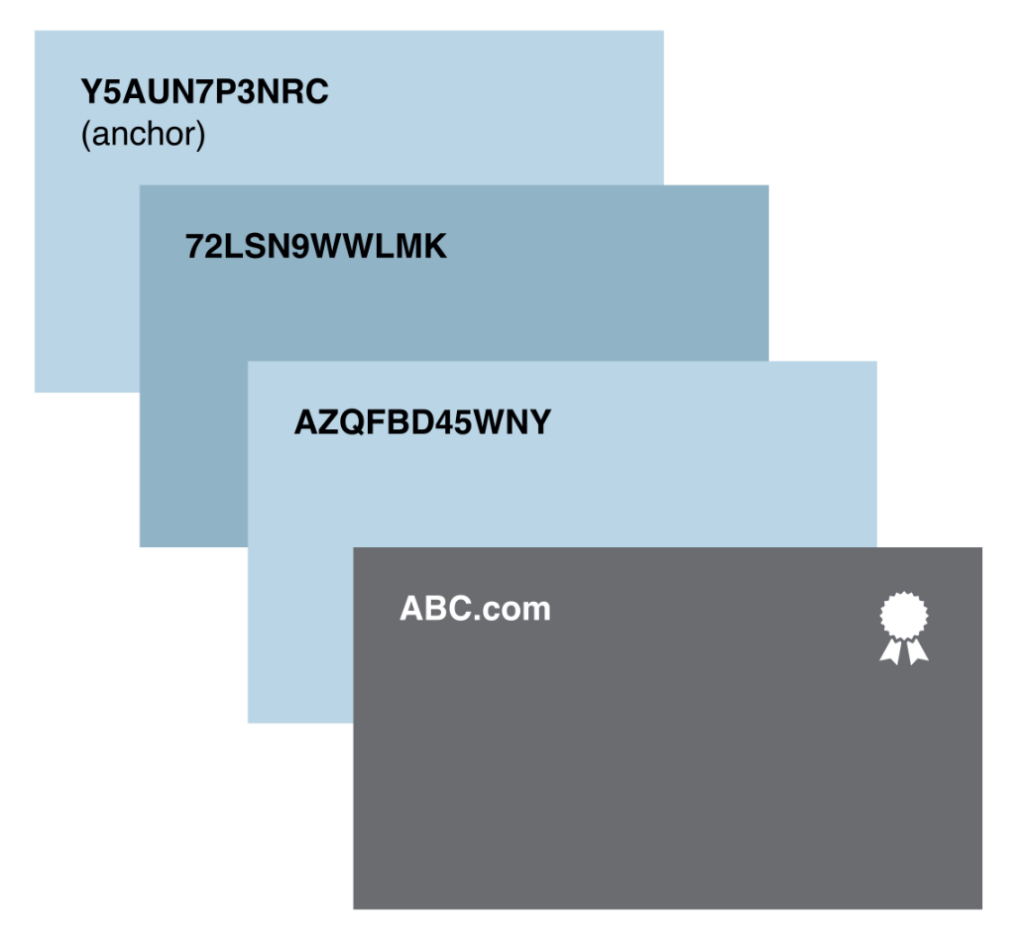
When establishing a TLS encrypted connection the relying party (web browser) examines the certificate’s certification path, which includes a chain of certificates starting from the issued certificate and leading up to a trust anchor. Each certificate in the chain is signed by the subsequent certificate, ultimately reaching a trust anchor.
Signature Verification
The relying party (Web Browser) uses the public key of each certificate in the certification path to verify the digital signature of the next certificate. This process continues until the trust anchor is reached.
The digital signature is a cryptographic value created by the CA using its private key, binding the certificate’s content to the CA’s identity. The client uses the CA’s public key to decrypt the digital signature, and if the decryption matches the certificate’s content, the signature is considered valid. This validation confirms that the certificate has not been tampered with and was indeed issued by the trusted CA.
Trust and Expiry Checks
The relying party checks if the trust anchor is included in its pre-installed trusted root certificates. It also verifies the expiration date of each certificate to ensure it is still valid.
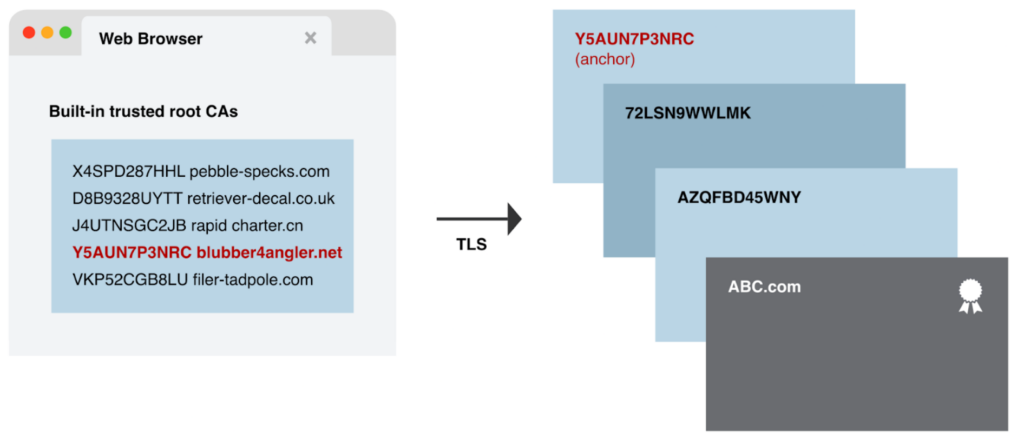
If the entire certification path is successfully validated, and the trust anchor is trusted, the relying party considers the certificate genuine and proceeds with the secure connection. With Couchbase Server 7.2.x this chain can be 10 certificates deep.
In this example, the built-in trusted root certificate authorities in the web browser are just made up names, but you can look at an actual list. Firefox pre-authorized trusted CAs are linked to from their wiki. If your certificate is generated by a CA that isn’t issued from one of the built-in trusted CAs, you will first need to add the CA’s public certificate as a trusted entity to your Operating System and Browser before you will be able to use certificates issued by that CA.
Now we’ve seen the components involved in TLS and how they work, in part 3 we’ll look at how TLS works in Couchbase Server.