Category: Best Practices and Tutorials
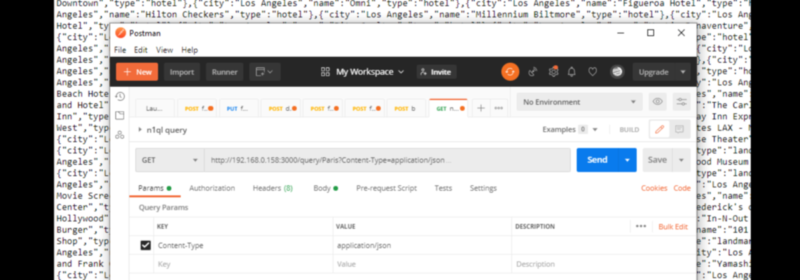
How to Query JSON Data Using SQL++ for Node.js and Couchbase
Today’s the day your Node.js app learns “go fetch.” By following this basic tutorial, you’ll learn how to build a REST API for your Node.js app that sends SQL++ (aka N1QL) queries to retrieve data from Couchbase. This post continues...
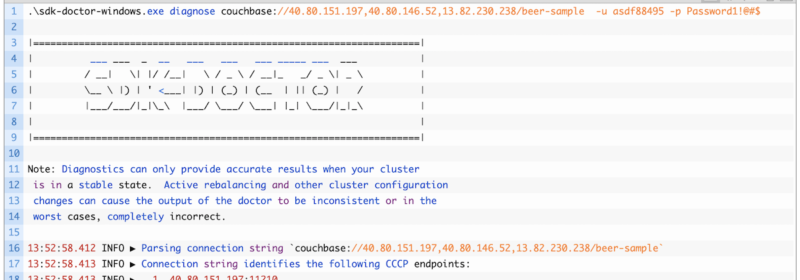
How to Troubleshoot Your SDK Connection using SDK Doctor & Couchbase Alternate Addresses
It’s a common experience to run into network connection errors when you’re developing an application – particularly if you’re connecting from your local computer SDK to a remote cluster. Is your SDK not connected? You’re likely to run into situations...

Secure Your Data at Rest with LUKS Disk Encryption in Couchbase
Couchbase now supports LUKS disk encryption to secure your data at rest. How secure is LUKS? Couchbase 7.0 puts a big focus on security, debuting support for both role-based access control (RBAC) for Scopes and Collections, and encryption of at-rest...

The N1QL Query Language Now Has a Per-Request Memory Quota
Unlike other services, the SQL++ query language so far hasn’t had the option to adjust its memory footprint. Until now. With the release of Couchbase Server 7.0, the Query Service now includes a per-request memory quota. Background The principal reason...

Learn about All Things Cloud at Couchbase Connect
If you haven’t heard already, Couchbase ConnectONLINE is fast approaching. There are many reasons for you join this free two-day conference, but today I’m going to focus on one track: “All Things Cloud.” I believe you’ll find this track interesting...
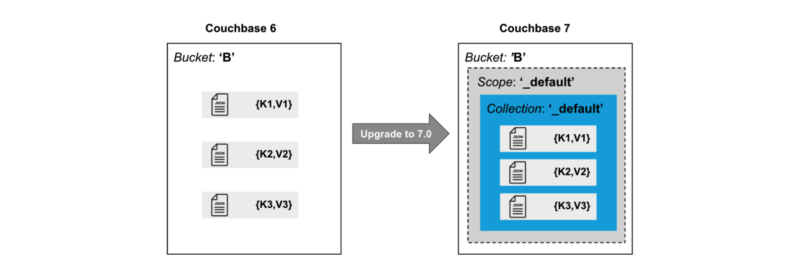
How to Migrate to Scopes & Collections in Couchbase 7.0
Whether you’re new to Couchbase or a seasoned vet, you’ve likely heard about Scopes and Collections. If you’re ready to try them out for yourself, this article helps you make it happen. Scopes and Collections are a new feature introduced...

5 Reasons for Developers to Attend Couchbase Connect
When it comes to online tech conferences, you’ve got options. Lots of options. If you’re a NoSQL developer, then Couchbase ConnectONLINE 2021 should be at the top of your list. This free two-day conference on 20-21 October 2021 has a...
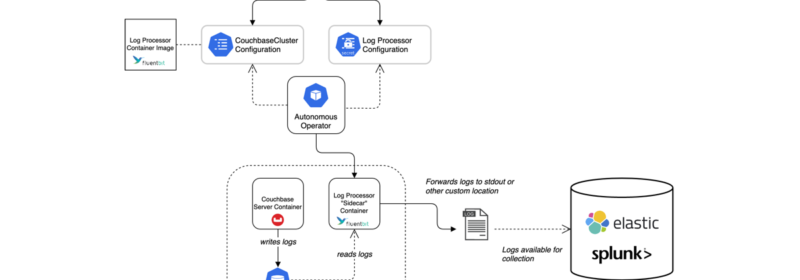
11 Fluent Bit Examples, Tips & Tricks for Log Forwarding with Couchbase
Log forwarding and processing with Couchbase is easier than ever. We have support for log forwarding and audit log management for both Couchbase Autonomous Operator (i.e., Kubernetes) and for on-prem Couchbase Server deployments. In both cases, log processing is powered...

How to Create Async Get/Upsert Calls with Node.js and Couchbase
If you’re a JavaScript dev who’s transitioning to use Node.js, you’ll want to take advantage of async functions. That’s because asynchronous API calls don’t block your code and return promises. In this post, I’ll show you how to create async...
![A Better Development Experience with Ottoman JS [Video]](https://www.couchbase.com/blog/wp-content/uploads/2021/08/ottoman-js-odm-couchbase-javascript-friends-conference-800x280.png)
A Better Development Experience with Ottoman JS [Video]
If you’re a JavaScript developer, I hope you know about the JavaScript & Friends conference. The JS & Friends conference is a diverse group of around 200 JavaScript developers and friends who get together to learn new skills and concepts...

Your Guide to User-Defined Functions in Couchbase Analytics
User-defined functions put you in the driver’s seat when it comes to querying and analyzing your data. In the Couchbase ecosystem, user-defined functions (UDFs) are reusable and parameterizable SQL++ queries that enable you to modularize queries and increase code reuse...

N1QL Now Supports User-Defined Functions
Declarative query languages have been a major gear shift in the world of database engines. The SQL++ query language (formerly N1QL) is primarily a declarative query language. You tell the query what to get and N1QL works out the rest...