This article aims to bring awareness around the importance of data encryption, considering the astounding rate at which data is being produced, transmitted and consumed. We will discuss the need for data protection, regulation, and some encryption best practices.
Organizations of all sizes across the globe are dealing with a staggering volume of data, ranging from personally identifiable information (PII) to protected health information (PHI), financial records, and other sensitive information that can quickly get out of control if not governed properly.
Data privacy protection is becoming a priority for individuals, organizations and governments alike. As governments work to get protection of data privacy rights under control, organizations are reconsidering how they collect, store and process personal information. Data encryption is one thing that can help organizations mitigate risks and stop data sprawl and cyberattacks before they occur.
What is data encryption?
Data encryption is a process in which plaintext information is scrambled into incomprehensible text known as cipher-text, using cryptographic modules known as secret keys that only authorized parties can understand. On the other hand, decryption is the process of converting cipher-text back to plaintext data using the same secret key.
There are two main kinds of data encryption standard: symmetric and asymmetric.
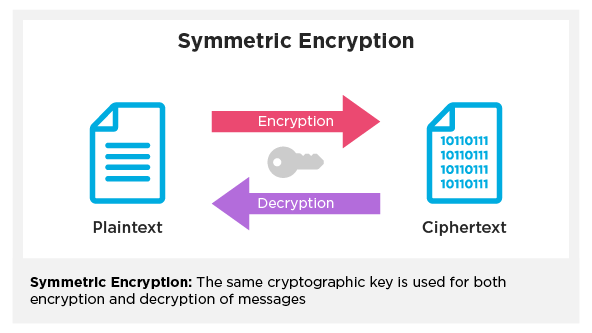
In symmetric encryption, developers use only one secret key for both encryption and decryption.
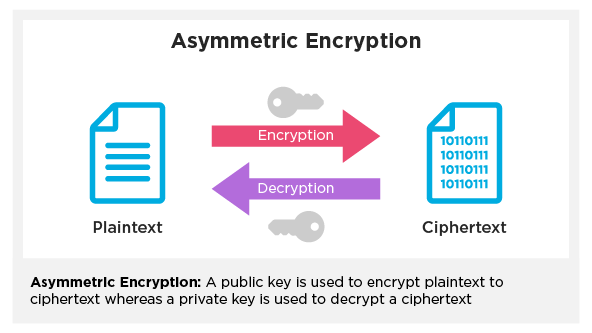
In asymmetric encryption, developers use two keys: a public key and a private key. There’s a public encryption key for anyone to use and a private decryption key that must be kept secret. Developers generally prefer asymmetric encryption over the wire — also known as “data encryption in transit” — using protocols like SSL and TLS.
Why data encryption is essential
Let’s take a look at some data breaches that occurred during 2020.
January 22: A customer support database holding over 280 million Microsoft customer records was left unprotected on the web. Microsoft’s exposed database disclosed email addresses, IP addresses, and support case details. Microsoft says the database did not include any other personal information.
February 11: Fifth Third Bank, a financial institution with 1,150 branches in 10 US states, claims a former employee was responsible for a data breach that exposed customer names, Social Security numbers, driver’s license information, mother’s maiden names, addresses, phone numbers, date of birth, and account numbers. The total number of affected employees and banking clients remains undisclosed.
April 6: A digital wallet app, Key Ring, stored customer data of 14 million users in an unsecured database. The app allows users to easily upload and store scans and photos of membership and loyalty cards to a digital folder in their mobile device. The exposed data included names, full credit card details (including CVV numbers), email address, birth date, address, membership ID numbers, retail club and loyalty card memberships, government IDs, gift cards, medical insurance cards, medical marijuana IDs, IP address and encrypted passwords.
June 23: A security lapse at Twitter exposed an undisclosed number of business users’ account information, including email addresses, phone numbers, and the last four digits of their credit card numbers.
This is not a comprehensive list, but it gives us an idea of the scale at which data breaches can occur, irrespective of the size, location, and type of organization.
According to IBM Cost of Data Breach Report 2020, the average cost of data breach in the United States alone is $8.64M. Most of these attacks expose customer PII, costing businesses an average of $150 per stolen record. Add to this indirect costs such as bad publicity and loss of consumer confidence. Data breaches can impact sales for years to come.
Overwhelming? This is where data encryption can make a difference.
A strong encryption:
- Ensures Data Privacy – No one but the rightful data owner can see actual data. The encrypted cipher-text is simply gibberish to unauthorized users.
- Provides Data Security – Proper encryption protects data in transit (over the wire) and data at rest. This is crucial in the event of a compromised network or a stolen physical storage disk.
- Maintains Data Integrity – In the case of man-in-the middle attacks, encryption (along with other security measures) ensures that data is not tampered with.
- Authenticates the origin of data, thereby assisting in sender verification.
This is all good to know, but is encryption mandatory? Is there any governance? Do data privacy laws, regulations and standards explicitly call for encryption? To get answers to these questions, let’s look at today’s most prevalent data privacy laws and standards.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a US federal law that requires the creation of national standards to protect sensitive patient health information (PHI) from being disclosed without the patient’s consent or knowledge. HIPAA requires organizations and covered entities to protect PHI for every patient. Regulators demand organizations encrypt their data unless they can justify why they can’t implement encryption and can provide an equivalent alternative.
The Payment Card Industry Data Security Standard (PCI DSS) was developed to secure and protect the entire payment card ecosystem. This standard requires companies to encrypt payment card data in transit and at rest.
The General Data Protection Regulation (GDPR) is a law on data protection and privacy in the European Union and the European Economic Area. Its primary aim is to give individuals control over their personal data and to simplify the EU regulatory environment. GDPR requires organizations to incorporate encryption and thereby mitigate the risks associated with a data breach.
The California Consumer Privacy Act (CCPA) is a state-wide data privacy law that regulates how businesses all over the world are allowed to handle the personal information (PI) of California residents.
Governing organizations have proven willing to fine organizations for data breaches, especially when incidents involve “non-encrypted or non-redacted personal information”. Regulators are more likely to waive responsibility when organizations make an effort to use encryption. They may also forgive when affected data is of no use without the decryption key.
Data encryption best practices:
Now that we know what encryption is, how it works, how it can mitigate damage, and the different regulations around it, let’s look at the best ways to implement data encryption to avoid mishaps and loopholes that can make your organization vulnerable to a data breach.
Here are some recommended practices:
- Work with stakeholders Identify all stakeholders and establish their roles in securing data, especially those who have actual data access. Next, identify what information needs protecting. This is a very important step towards securing your data.
- Identify the encryption tool whatever secret key / encryption algorithm you choose should follow established standards and frameworks such as FIPS, ISO/IEC 27000, or NIST, such that a third party is unlikely to break the cipher-text by brute force.
- Secure encryption keys securing your keys to keep them out of the hands of unauthorized users is critical. Here are some basic steps to protect your keys:
-
-
- Separate encrypted data from keys.
- Don’t store the key in a plaintext file.
- Provide privileges only to authorized users.
- Rotate keys on a regular basis.
-
- Protect data at all times Organizations must plan to protect data in transit and at rest. To enable data encryption at rest, encrypt sensitive files prior to storing them and/or encrypt the storage media itself. To protect data in transit, they can install SSL/TLS certificates on their servers.
Conclusion
Data encryption is an important part of information security. The consequences of a data breach can be wide-ranging: from regulatory penalties to economic losses. Adopting encryption as a best practice is the simplest and most effective way for organizations to mitigate these impacts .We hope this article has given you some information about the importance of encryption and the governance around it, and helped you make some important decisions about information security.
References
https://www.identityforce.com/blog/2020-data-breaches
https://www.securitymetrics.com/blog/what-are-12-requirements-pci-dss-compliance
