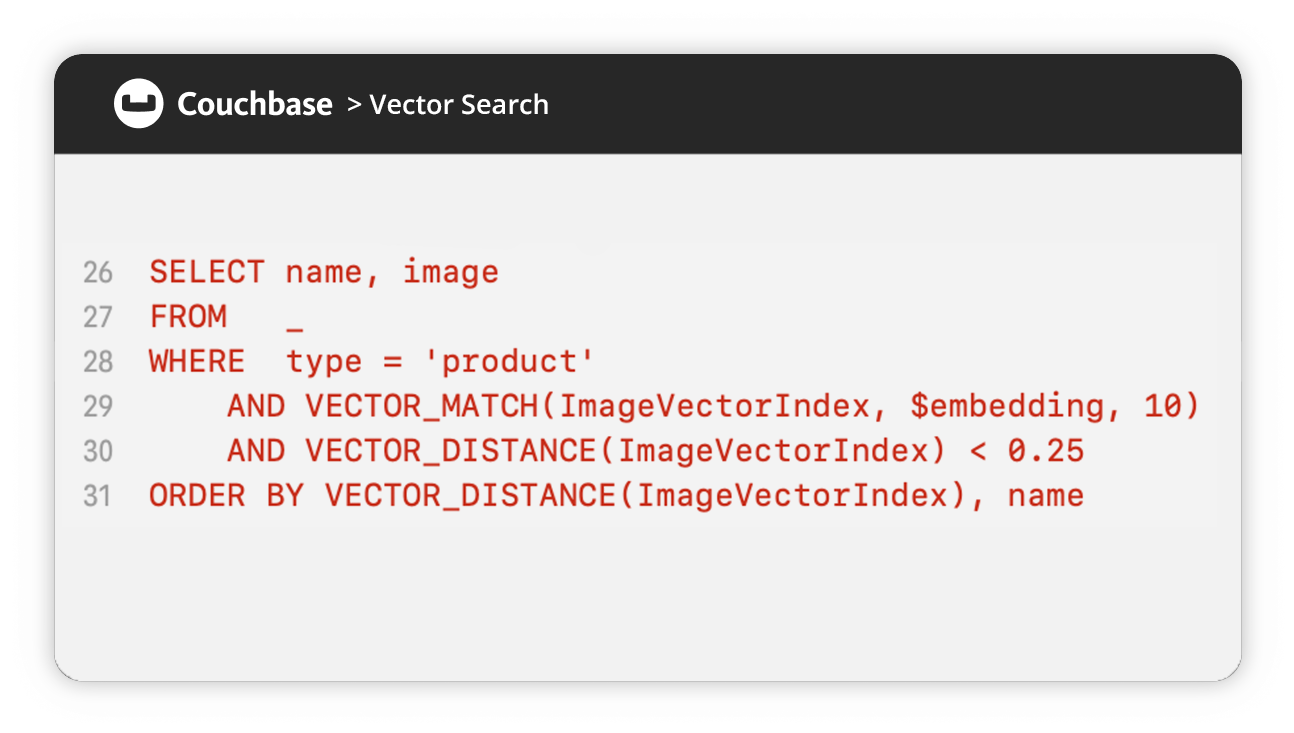
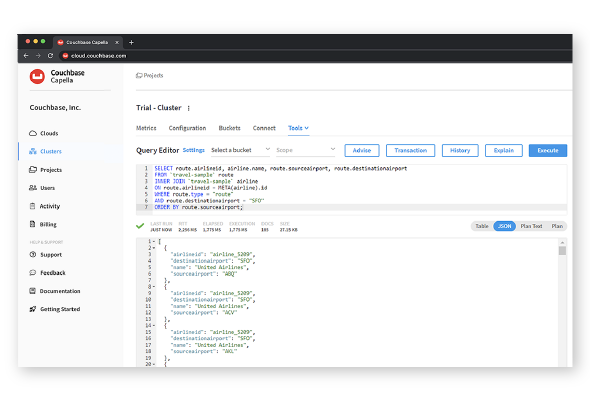
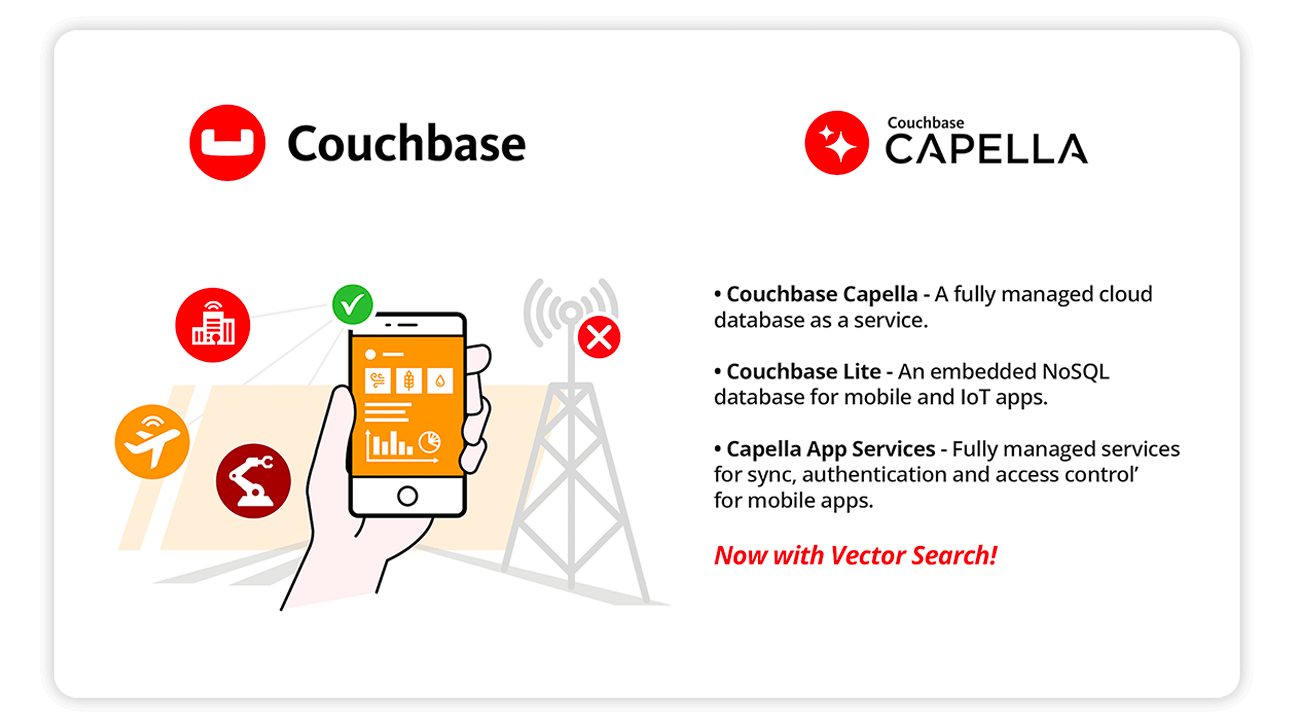
This page lists critical alerts and advisories for Couchbase.
| CVE | Synopsis | Impact (CVSS) | Products | Affects Version | Fix Version | Publish Date |
|---|---|---|---|---|---|---|
|
Query Service stats endpoint was accessible without authentication. |
Medium |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
User with Data Reader role could OOM kill the Data Service. |
Medium |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Data readers could DOS the reader threads. |
Medium |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Unauthenticated RMI Service Ports Exposed in Analytics Service. |
Critical |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
otpCookie was shown to a user with a Full Admin role on the Cluster Manager's API endpoints serverGroups and engageCluster2. |
High |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
SQL++ cURL calls to /diag/eval were not sufficiently restricted. |
High |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
SQL++ N1QL cURL host restrictions implementation issue. |
Medium |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Eventing SQL++ cURL calls to /diag/eval were not sufficiently restricted. |
High |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
The internal Full Admin user for cluster management credentials leaked to log file. |
Low |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
TLS Private key leaked in XDCR log file. |
Low |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Upgrade cURL to 8.4.0. |
Critical |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Upgrade to OpenSSL 3.1.4. |
Medium |
Couchbase Server |
Server |
Server |
January 2024 |
|
|
Upgrade gRPC to v1.58.3. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Upgrade Golang to 1.20.10. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Upgrade to OpenSSL 1.1.1u. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Update of GoLang to 1.19.9. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Update V8 to 11.4.185.1. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
CVE-2023-21930 |
Update OpenJDK to 11.0.19. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
Windows traversal security issue. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Unauthenticated users may cause memcached to run out of memory. |
High |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Private key leak in debug.log while adding pre-7.0 node to 7.2 cluster. |
Medium |
Couchbase Server |
Server |
Server |
November 2023 |
|
|
Update Netty to 4.1.86.Final or higher. |
Low |
Couchbase Server |
Server |
Server |
May 2023 |
|
|
Full Text Search (FTS) nsstats endpoint is accessible without authentication. |
Medium |
Couchbase Server |
Server |
Server |
March 2023 |
|
|
Credentials can be leaked to the logs if there is a crash during a node join. |
Medium |
Couchbase Server |
Server |
Server |
January 2023 |
|
|
Couchbase Cluster Manager lacks access controls during a cluster node restart. |
Critical |
Couchbase Server |
Server |
Server |
January 2023 |
|
|
Update of Jackson Databind to 2.13.4.2+ as used in the Analytics Service to resolve vulnerabilities. |
High |
Couchbase Server |
Server |
Server |
January 2023 |
|
|
A crafted HTTP request to REST API can cause a backup service OOM. |
Medium |
Couchbase Server |
Server |
Server |
January 2023 |
|
|
Update of V8 Javascript Engine to 10.7.x. |
High |
Couchbase Server |
Server |
Server |
January 2023 |
|
|
Update of Apache Parquet to 1.12.3. |
High |
Couchbase Server |
Server |
Server |
November 2022 |
|
|
Upgrade of Erlang to version 24.3.4.4. |
Critical |
Couchbase Server |
Server |
Server |
November 2022 |
|
|
Private key is leaked to the log files with certain crashes. |
Medium |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Update of GoLang to a minimum of 1.17.9 or 1.18.1. |
High |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Update of jackson-databind library to version 2.13.2.2. |
Medium |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Update of openssl to 1.1.1o. |
Critical |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Encrypted Private Key passphrase may be leaked in the logs. |
Medium |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Updating ramda, a client-side javascript library to version 0.28 as used in the Couchbase Server UI. |
Critical |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Update of js-beautify to 1.14.3, a client-side javascript library used in the Couchbase Server UI. |
Critical |
Couchbase Server |
Server |
Server |
July 2022 |
|
|
Field names are not redacted in logged validation messages for Analytics Service. |
Low |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Analytics Remote Links may temporarily downgrade to non-TLS connection to determine TLS port. |
Low |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Backup Service log leaks unredacted usernames and doc ids. |
Low |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Update golang.org/x/text package to 0.3.4 or later. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
couchbase-cli leaks Secrets Management master password as a command-line argument. |
Medium |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Operations may succeed on collection using stale RBAC permission. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
XDCR - lacks role checking when changing internal settings. |
Medium |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
couchbase-cli: server-eshell leaks the Cluster Manager cookie. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Python updated to 3.9.12 to address a denial of service issue. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Sample bucket loading may leak internal user passwords during a failure. |
Medium |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Private key may be logged during a crash of the Cluster Manager component of Couchbase Server. |
Medium |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Previous mitigations for CVE-2018-15728 were found to be insufficient when it was discovered that diagnostic endpoints could still be accessed from the network. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Index Service does not enforce authentication for TCP/TLS servers. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Random http requests lead to leaked metrics. |
High |
Couchbase Server |
Server |
Server |
June 2022 |
|
|
Admin credentials not verified when using X.509 client cert authentication from Sync Gateway to Couchbase Server. |
Critical |
Couchbase Sync Gateway |
Couchbase Sync Gateway: |
3.0.2 |
June 2022 |
|
|
Untrusted node addition can be manipulated in order to harvest a cluster secret. |
High |
Couchbase Server |
Server |
Server |
May 2022 |
|
|
Secrets not redacted in logs collected from Kubernetes environments. |
High |
Couchbase Cloud Native Operator |
2.2.0, |
2.2.3 |
March 2022 |
|
|
Update of Apache Log4J to 2.15.0 |
Critical |
Couchbase Server |
Server |
Server |
December 2021 |
|
|
Sync Gateway insecurely stores Couchbase Server bucket credentials |
Medium |
Couchbase Sync Gateway |
Sync Gateway |
Sync Gateway 2.8.3 |
October 2021 |
|
|
Logs not redacting XDCR remoteCluster credentials |
High |
Couchbase Server |
Server |
Server |
October 2021 |
|
|
Credentials exposed in crash error log from a backtrace |
High |
Couchbase Server |
Sever |
Server |
October 2021 |
|
|
Update of the Python urllib3 to 1.26.5 or higher |
High |
Couchbase Server |
Server |
Server |
October 2021 |
|
|
Update of the Python cryptography package to 3.3.2 |
Critical |
Couchbase Server |
Sever |
Server |
October 2021 |
|
|
A specially crafted network packet sent from an attacker can crash memcached |
High |
Couchbase Server |
Server |
Server |
September 2021 |
|
|
A specially crafted network packet sent from an attacker can crash memcached |
High |
Couchbase Server |
Server |
Server |
September 2021 |
|
|
Externally managed users are not prevented from using an empty password, per RFC4513 |
Critical |
Couchbase Server |
Server |
Server 6.6.3 |
August 2021 |
|
|
Update OpenSSL to version 1.1.1k |
Medium / High |
Couchbase Server |
Server |
Server 6.6.3 |
August 2021 |
|
|
Update AngularJS to 1.8.0 |
High |
Couchbase Server |
Server |
Server 6.6.3 |
August 2021 |
|
|
N1QL Common Table Expressions (CTEs) handled access control incorrectly. |
Medium |
Couchbase Server |
Server |
Server 6.6.2 |
February 2020 |
|
|
FTS UI to upgrade to angular 1.6.9 |
High |
Couchbase Server |
6.0.2, |
6.5.0 |
January 2020 |
|
|
Up until core-io 1.7.11 (and as a result Java SDK 2.7.11), hostname verification on TLS/SSL connections is not enabled and can be a security risk in certain environments |
High |
Couchbase Java SDK |
1.7.10, |
2.7.11 |
April 2019 |
|
|
Projector and indexer REST endpoints did not require authentication |
High |
Couchbase Server |
5.5.1, |
6.5.0 |
September 2018 |
|
|
Couchbase Server returns a WWW-Authenticate response to unauthenticated requests |
Medium |
Couchbase Server |
6.0.0 |
6.5.1 |
April 2020 |
|
|
Port 8092 misses X-XSS protection header |
Medium |
Couchbase Server |
5.5.0 |
6.0.2 |
March 2019 |
|
|
Prevent N1QL injection in Sync Gateway via _all_docs startkey, endkey |
High |
Couchbase Sync Gateway |
2.1.2 |
2.5.0 |
February 2019 |
|
|
Eventing debug endpoint must enforce authentication. |
High |
Couchbase Server |
6.0.0 |
6.0.1 |
December 2018 |
|
|
Memcached "connections" stat block command emits non-redacted username |
Medium |
Couchbase Server |
6.0.0, |
6.0.1 |
January 2019 |
|
|
The /diag/eval endpoint is not locked down to localhost. |
High |
Couchbase Server |
5.5.1, |
6.0.0 |
October 2018 |
|
|
Erlang cookie uses a weak random seed. |
High |
Couchbase Server |
5.1.1 |
6.0.0 |
September 2018 |
|
|
JSON doc with >3k '\t' chars crashes indexer. |
Medium |
Couchbase Server |
5.5.0, |
5.1.2, |
August 2018 |
|
|
XDCR does not validate a remote cluster certificate. |
High |
Couchbase Server |
5.0.0 |
5.5.0 |
June 2018 |
|
|
Editing bucket settings in Couchbase Server allows authentication without credentials. |
High |
Couchbase Server |
5.0.0 |
5.1.0 |
December 2017 |